[Important] Revert changes to docker setup
| If you are running a Percept version below 1.4.1, we highly recommend to upgrade to a version 1.4.1 or higher because starting with 1.4.1 we changed to a more secure method of interacting with Docker. |
Windows
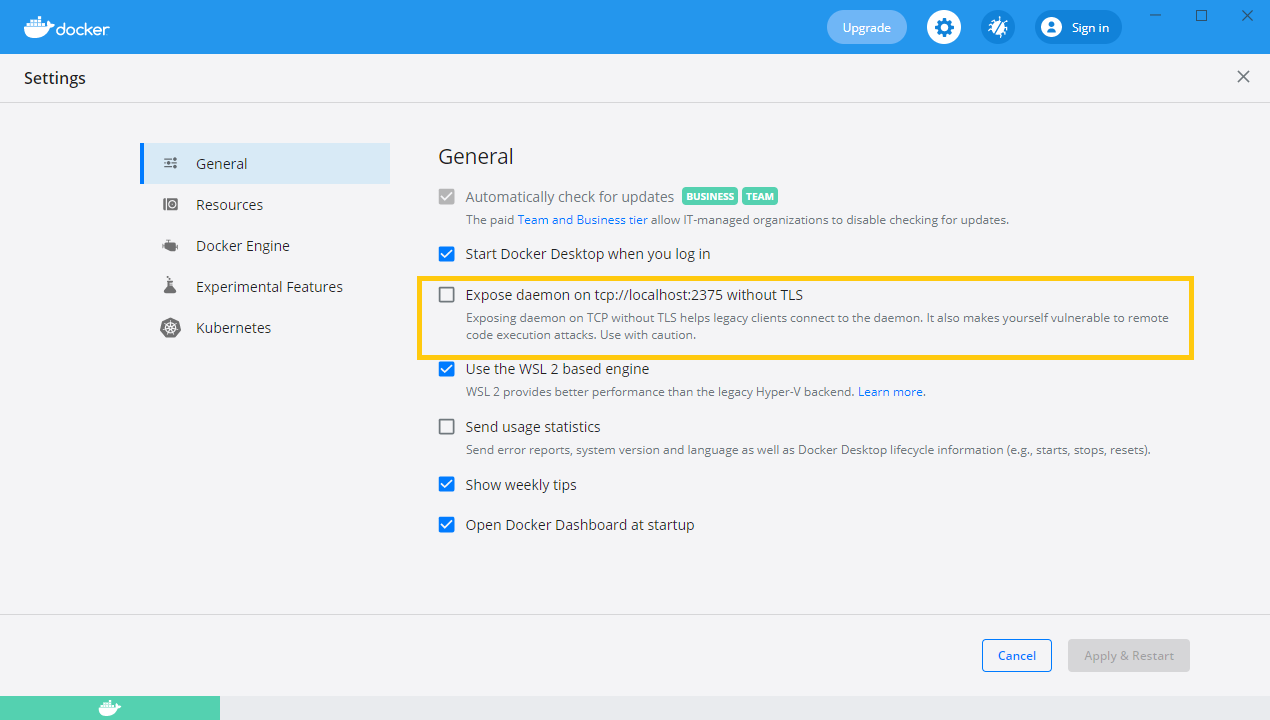
In order to close the open tcp port on Windows, make sure to untick the option “Expose daemon on tcp://localhost:2375 without TLS” in the docker GUI (see picture).
Ubuntu
On Ubuntu systems we used to change the configuration on the docker daemon by running a custom configure script. In order to create a clean docker environment, these files have to be removed and the docker service has to be restarted.
We provide two options for reverting the changes on the system. You can choose either to run the clean up script, which is shipped with Percept or running every command in the command-line (advanced). As a last step, make sure to follow the instructions for Verifying clean docker setup.
If you use docker for other applications on your system reverting the docker daemon configurations can have an effect on those. Make sure to check the content of etc/docker/daemon.json and compare them with the content we added, see Configuration files in Percept <= v1.4.0. If you encounter differences to our setup please follow the steps in Option 2. Revert changes manually using command line (advanced) instead of Option 1. Using the script to revert changes.
|
Option 1. Using the script to revert changes
If you are using Percept as the only container based application please use the script.
In order to get a clean system run the fix_docker_setup.sh script in a terminal (needs root permission). It will clean up the modified directories and restart the docker daemon.
-
sudo ./fix_docker_setup.sh
The individual steps of the script are shown below:
-
Delete the file docker daemon configuration file:
rm /etc/docker/daemon.json -
Revert the changes made to the docker service:
systemctl revert docker.service -
Editing system unit files requires reloading the daemon:
systemctl daemon-reload -
Restart docker socket:
systemctl restart docker.socket -
Restart docker service:
systemctl restart docker.service
Option 2. Revert changes manually using command line (advanced)
If you have other applications that use Docker on your system then follow these steps.
This chapter contains a more detailed description of the changes required to upgrade from Percept version <= 1.4.0. We recommend only people who have a deeper understanding of Docker to follow this guide. If this is not the case, please use Option 1. Using the script to revert changes or contact us. In the following steps are presented to clean up the Docker setup:
-
In Percept version <= v1.4.0, we use the Docker Engine API to launch additional subcomponents as Docker containers. This requires making the Docker Engine API accessible from our main Docker container. The method we chose for this on Linux operating systems caused the Docker Engine API to bind to port 2375 on all network interfaces (
"tcp://0.0.0.0:2375"). Due to the architecture of Docker, access to this port can enable remote or local attackers to execute code or escalate their privileges. In most typical installations, a firewall or router prevents direct access to this port, leaving only internal users on the same network or the same machine as potential attackers. Check the etc/docker/daemon.json on your system and compare it our changes shown in Configuration files in Percept <= v1.4.0. In Percept version > 1.4.0 we do not need this configuration anymore. You can either remove the entire file (rm /etc/docker/daemon.json) or remove thehostsentry.This action might have an effect on other containers running on your system, if they are using this mechanism for intercommunication between the container and the docker daemon. We advice against using this mechanism due to the aforementioned security risk. -
In order to run a docker daemon with specified
hostsfor Percept version <= 1.4.0, we had to overwrite the configuration (see content of/etc/systemd/system/docker.service.d/docker.confin Configuration files in Percept <= v1.4.0) for systemd to be started without the -H flag. A more detailed description can be found on the docker homepage: Use the hosts key in daemon.json with systemd. In Percept version > 1.4.0 this configuration is not needed anymore. You can revert this configuration withsystemctl revert docker.service.This action might have an effect on other containers running on your system, if they are using this mechanism for intercommunication between the container and the docker daemon. We advice against using this mechanism due to the aforementioned security risk. -
As a last step the changed configurations have to be applied for the docker service. For that you can just use the following three commands:
-
systemctl daemon-reload -
systemctl restart docker.socket -
systemctl restart docker.service
-
| The docker.socket has to be restarted, since settings to the tcp port have changed! |
Configuration files in Percept <= v1.4.0
We want to ensure that your system is able to run other applications next to Percept. We changed the configuration of the docker daemon by modifying two files (/etc/docker/daemon.json and /etc/systemd/system/docker.service.d/docker.conf) in Percept versions <= v1.4.0.
| If the content on your system does not match with the content of these files do not follow the process from Option 1. Using the script to revert changes. Option 2. Revert changes manually using command line (advanced)! |
Content of /etc/docker/daemon.json:
{
"log-driver": "json-file",
"log-opts": {"max-size": "100m", "max-file": "10"},
"hosts": [
"tcp://0.0.0.0:2375",
"unix:///var/run/docker.sock"
]
}Content of /etc/systemd/system/docker.service.d/docker.conf:
[Service]
ExecStart=
ExecStart=/usr/bin/dockerdVerifying clean docker setup
In order to verify a cleaned up docker daemon you can check it by typing docker info in a terminal. It displays system wide information regarding the Docker installation and information about kernel version, number of containers and images. Make sure that at the end of the output no warning as the following is present:
WARNING: API is accessible on http://0.0.0.0:2375 without encryption.
Access to the remote API is equivalent to root access on the host. Refer
to the 'Docker daemon attack surface' section in the documentation for
more information: https://docs.docker.com/go/attack-surface/Run Percept with open tcp port (strongly not recommended)
| Blickfeld advices against the configurations described in this section due to security risk. Use this only for systems where it cannot be avoided, e.g. when other applications use an open port for their communication between containers and the docker daemon. Docker Daemon Attack Surface |
If you are sure that you want to run Percept with an unsecure Docker setup (against our recommendation and aforementioned warning), you can modify the docker-compose.yml file. For that, add the variable ALLOW_DOCKER_UNSECURE_TCP_MODE: 'True' to the environment of the server.