Senstar
This section provides information on how to integrate QbProtect with Senstar Symphony.
|
The following Senstar Symphony components have been used in the examples below:
|
Add Device
The WebGUI of Senstar Symphony Server is used in order to add QbProtect into Senstar Symphony VMS as shown in the Figure below.
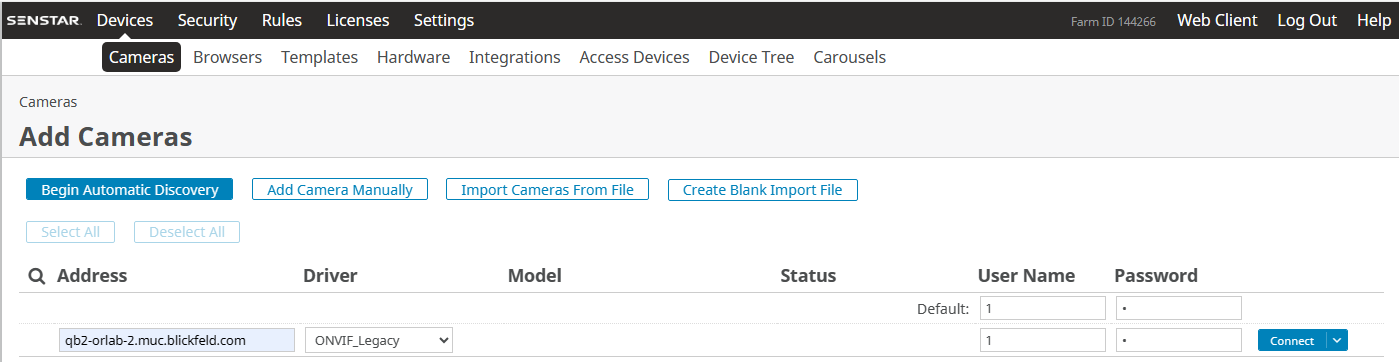
The procedure includes the following steps:
-
Navigate to
Devices→Cameras→Add Camera Manually. -
Enter the FQDN or IP of QbProtect in the address field
-
Select the
ONVIF_Legacydriver in the driver section -
Provide ONVIF credentials in user name and password fields correspondingly
-
Click
Connect -
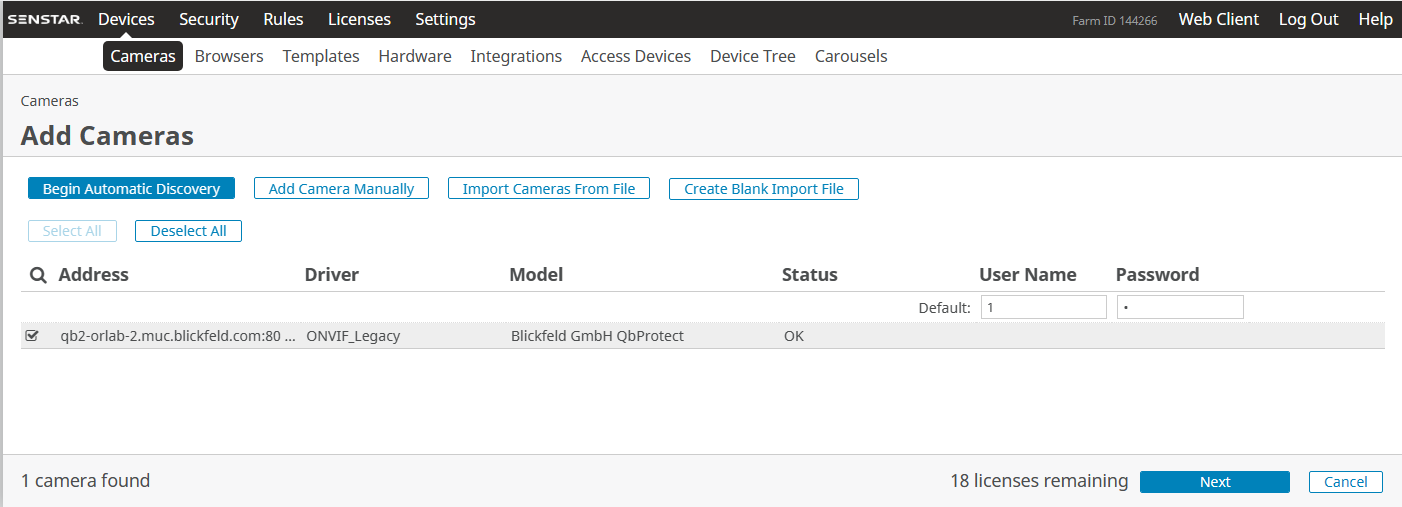
If the connection was succesfull the QbProtect device should be detected with
OKstatus -
Click
Next→ give name to the device → clickAdd 1 Selected Camera→ Wait till device is added
|
The ONVIF autodiscovery feature is not yet supported by QbProtect |
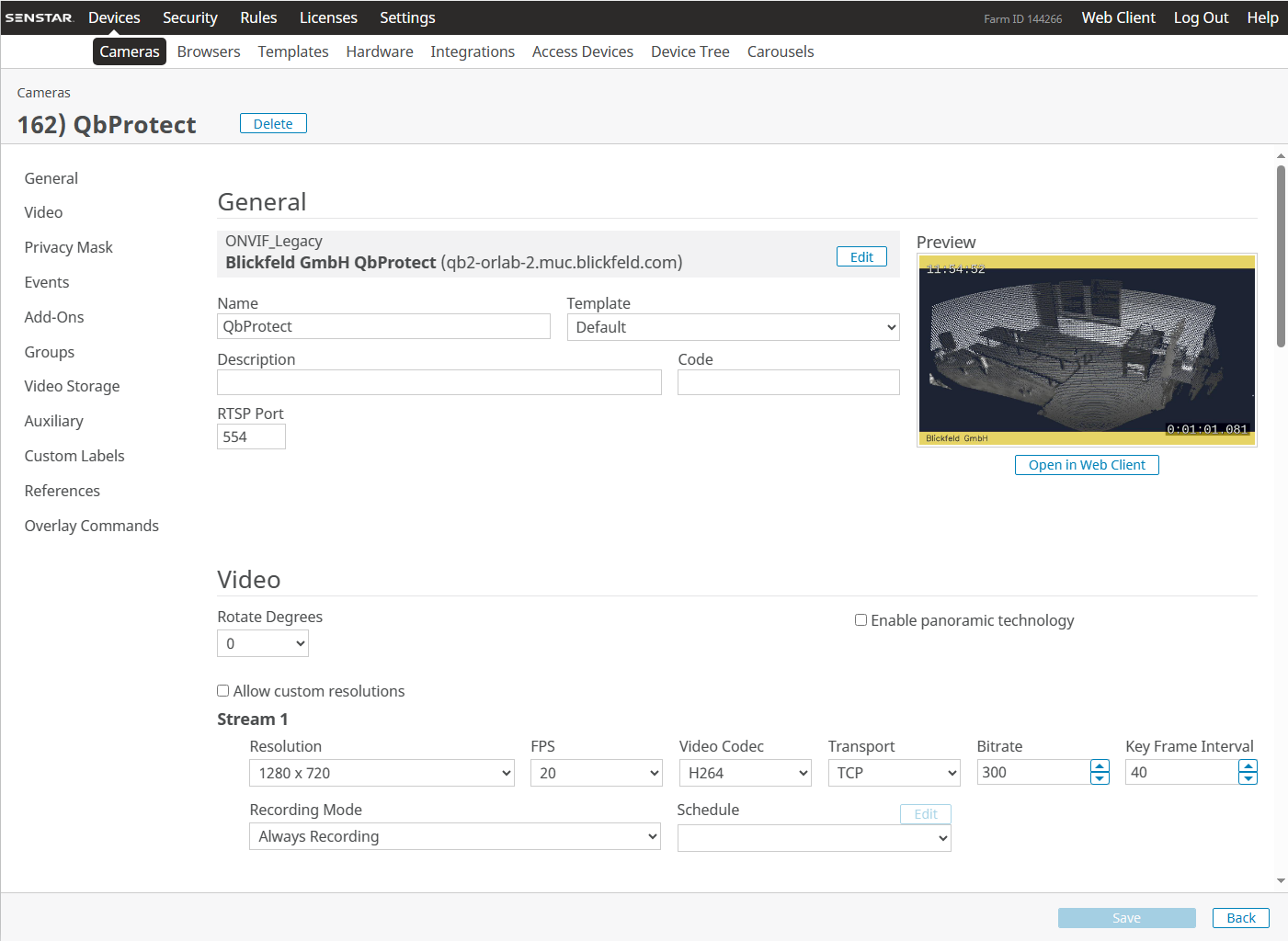
The General device view should depict the general information about the device, current video stream settings and the video stream preview as shown in the Figure below.
|
The video stream settings are currently static and their change won’t make any influence on the video stream |
From now on the live video stream of the point cloud can be accessed and observed in Symphony Client or its web version.
Events
Configure Alarms
The example below shows how QbProtect events can be used in Senstar Symphony. Supported events can be found in the corresponding Events view of Senstar Server as shown in the Figure below.
|
The examplified configuration procedure is unified by the VMS and, with minor adaptations, can be followed to make use of any event supported by QbProtect. |
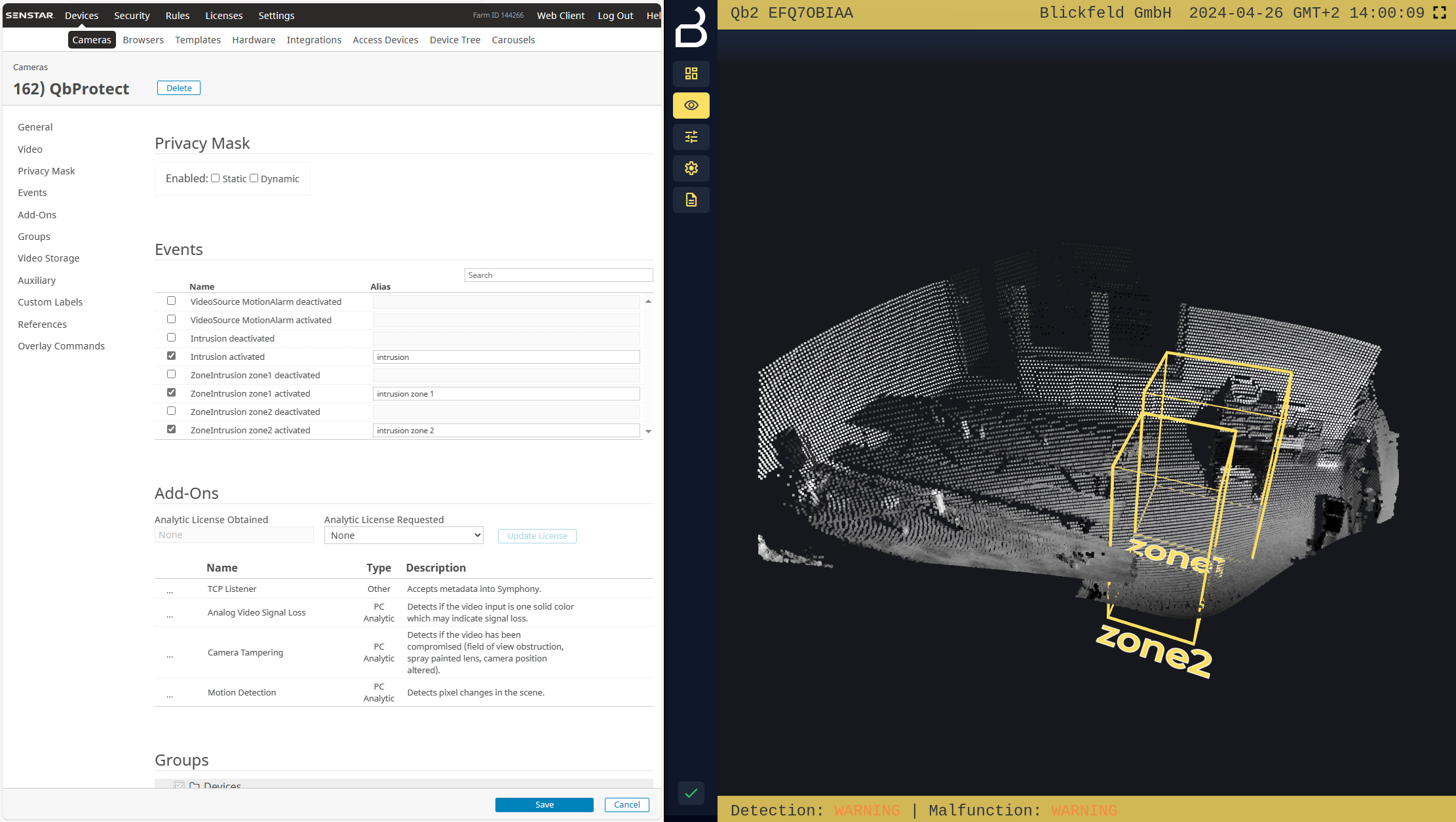
In this example two security zones zone1 and zone2 have been configured using QbProtect WebGUI. Therefore, in addition to the aggregated intrusion and motion events, two intrusion events for the corresponding intrusion zones can be found in the exposed event list.
Rule Chain
The chain consists of event, action and schedule. It allows to map a dedicated action (e.g. manual alarm action, .etc) to the event of the particular type (e.g. intrusion in security zone). This mapping operates according to the pre-configured time schedule (e.g. on the daily basis). The named rule chain configuration procedure consists of the following steps:
-
Activate events from the list of the exposed events in order to make use of them in rule chains. In this scenario, as shown in the Figure above, we have activated three event types: aggregated intrusion, intrusion in
zone 1andzone 2. -
Select active event as rule chain event source. Activation example for aggregated intrusion event is shown in the Figure below.
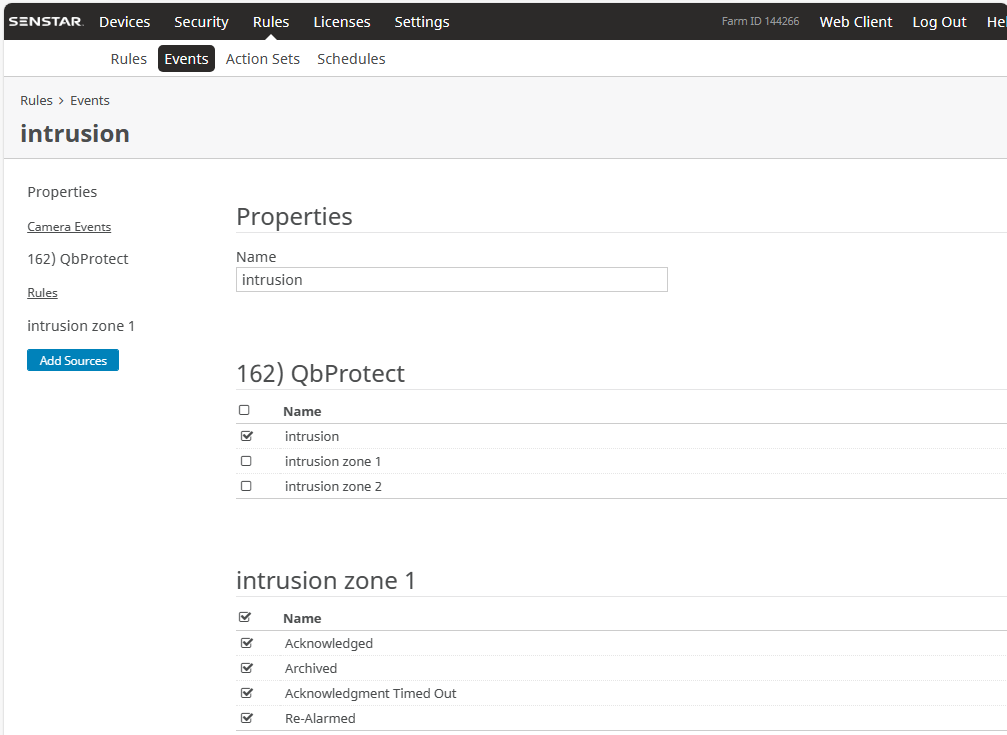 Figure 5. Select active QbProtect event as a source for Senstar Symphony rule chain
Figure 5. Select active QbProtect event as a source for Senstar Symphony rule chain -
Configure an action which will be executed by the rule chain whenever the event is coming from the configured event source. In this scenario it will be a manual alarm action, as shown in the Figure below.
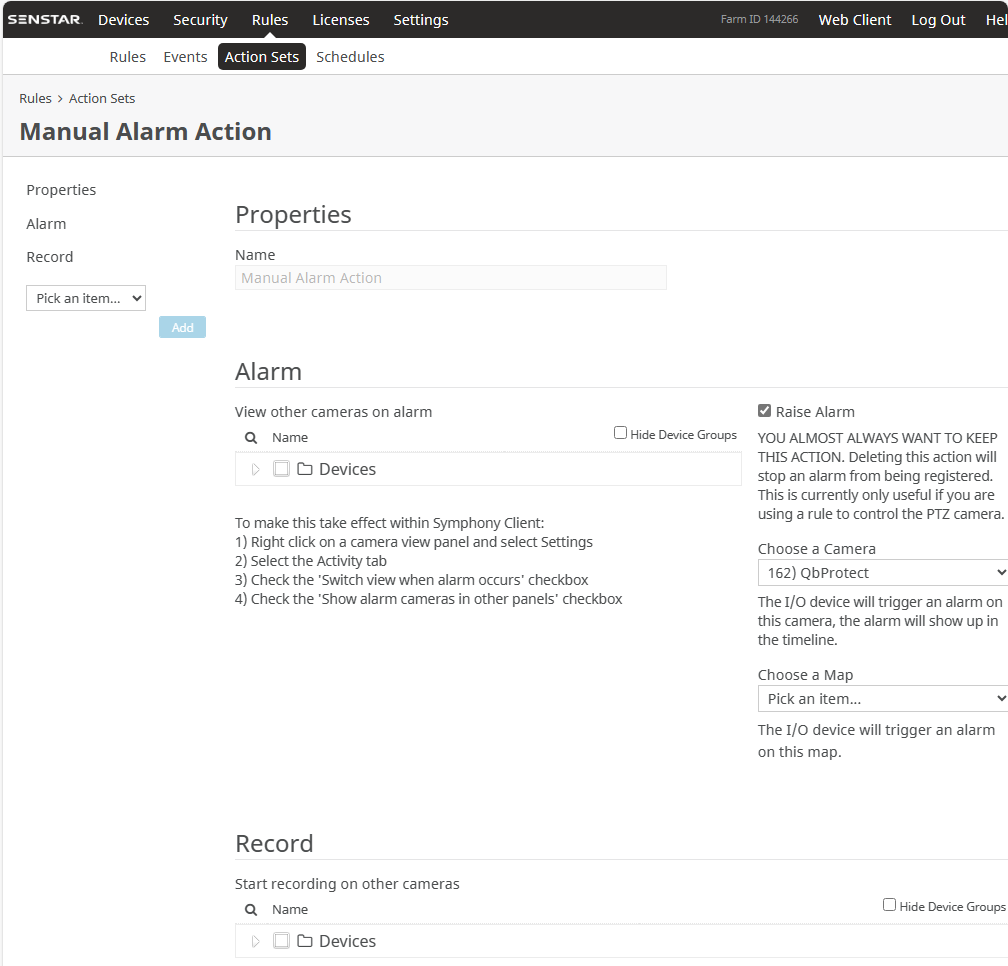 Figure 6. Manual alarm action configuration
Figure 6. Manual alarm action configuration -
Select the desired time schedule
Three rule chains (for aggregated intrusion, intrusion in zone 1 and zone 2) have been configured and enabled in this example as shown in the Figure below.
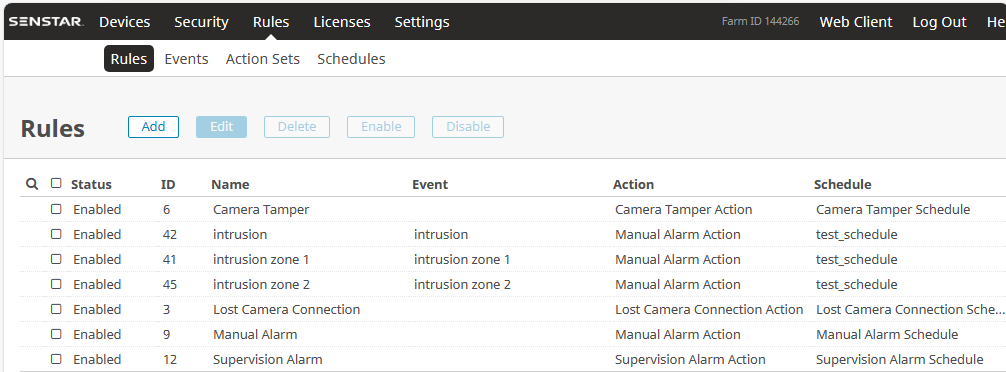
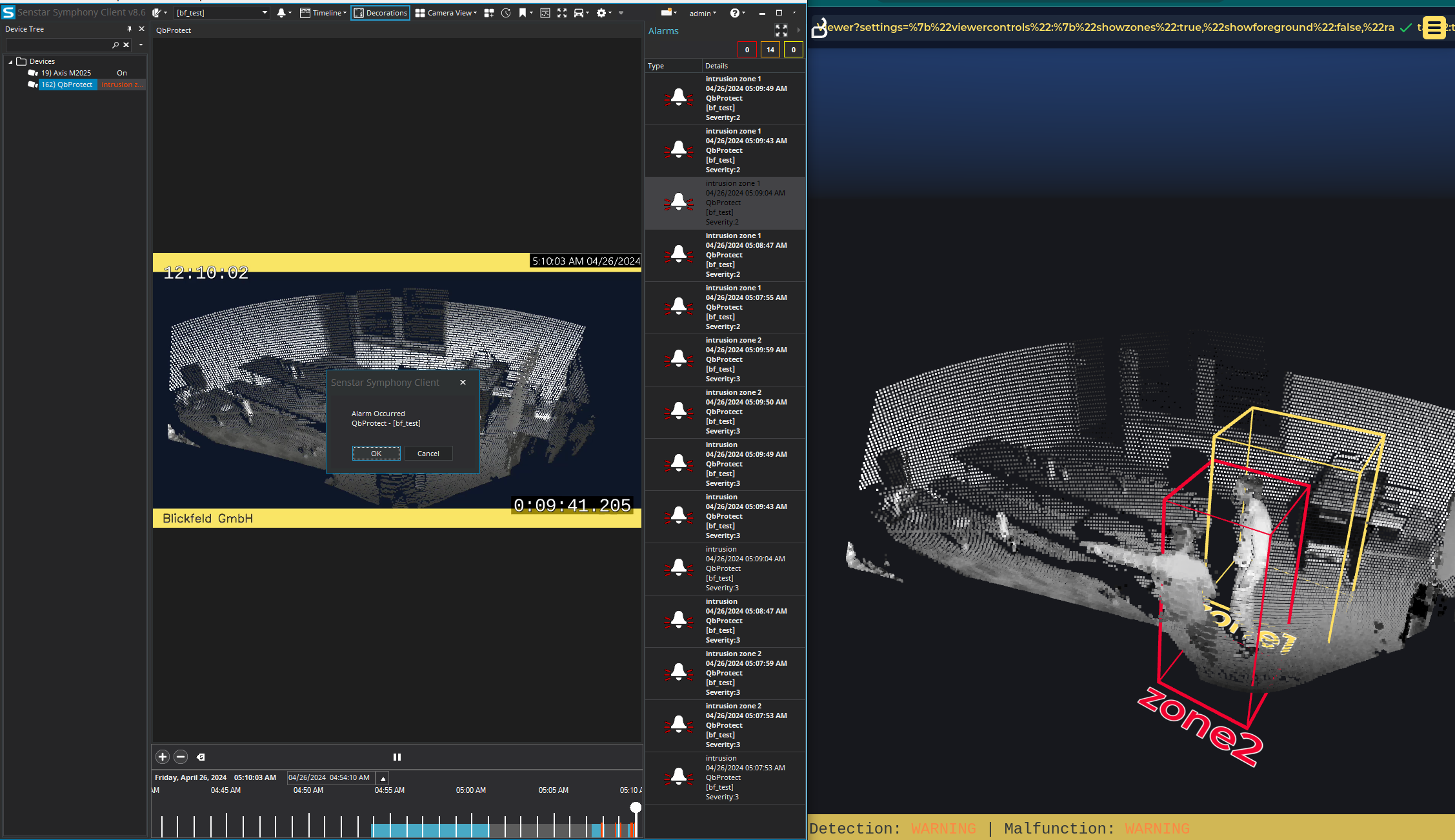
From now on, the aggregated intrusion alarm is raised when intrusion happens in either of the configured security zones in addition to the alarms raised per zone basis. The demonstration of zone 2 intrusion alarm raised inside Senstar Symphony client is shown in the Figure below.